Securing your confidential business and customer data is of paramount importance, especially in the ever-evolving landscape of cloud computing. In the realm of Azure Cloud, ensuring robust Security in Azure Cloud is not just a best practice; it’s a necessity. As businesses increasingly rely on this public cloud service, understanding its unique features and potential security challenges is crucial to safeguarding your digital assets. In this guide, we’ll navigate through the intricacies of securing applications on Azure Cloud, addressing everything from Denial-of-Service attacks to potential threats from both internal and external sources.
Join us on this journey towards fortifying your digital presence with the best practices in Security in Azure Cloud.
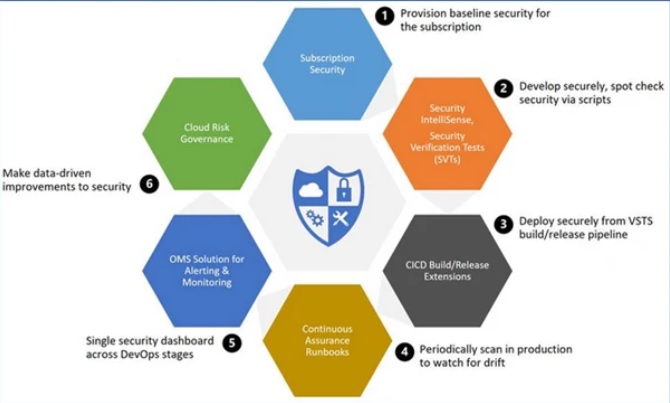
What are the challenges to application security in Azure Cloud?
Below are the enlisted Challenges to Application Security in Azure:
- Internal and External Data Access: Applications face complexity in accessing data peculiarly because of varied data sources. Rights to the application users require monitoring.
- Denial of Service (DoS) Attack: This is damaging as it prohibits the genuine users from reaching your website and servers. Denial of service can also be concealment for other malicious activities.
- Account Hijacking: Attackers have enough information about logins that is a threat to the sensitive data stored on the cloud. Hijackers capture and manipulate the credentials. If login information is at risk, the data certainly is at high risk. The scripting bugs and the unchanged passwords are of assistance to detect and steal credentials. Theft points are keylogging, buffer overflow, and user tokens that cloud platforms verify the devices for update or synchronization without login.
- Threats of negligence and human errors: Security in Azure requires proper understanding of security policy forming group and gaps of implementation is indirect threat. Low clarity of goals, untrained resources, and unclear policies contribute to the issues. Data migration on cloud contains anticipatory risks in case of security diligence. Insufficient information of regulatory laws pertaining to the individual’s rights, or proper exit formalities adds up to errors in handling data.
- Data Breach: Causes and consequences of data breach might be due to the ineffective contracts among the business parties. This includes unnecessary updates of restricted data, moving it without authorization; data upload or share against the terms and conditions. Data breach can call upon legal actions and regulators can levy penalties. In case of data breach of sensitive data placed on cloud the company needs to notify the victims. Loss of data by cyber attack is also data breach can damage the organization’s image.
- Data Loss: Vital information can be lost because of issues in cloud service provider agreement, hardware issues, and natural calamities (flood, lightning, and earthquake). Data needs detailed security plan to eliminate the risks.
- Theft of Intellectual Property: Security in Azure is must as companies store patents, trademarks, trade secrets, and sensitive data on cloud. The ownership issues attached to the data uploaded using certain services are debatable.
- Insecure applications: External applications, third party services, and non-suitability to your network are disputes to Security in Azure Cloud. No restriction on downloading new applications is an open invitation to threat.
- Unauthorized Access: Teamwork adds to productivity but teaming up to share passwords can be primary error. Blunders await such opportunities where easy access lets in the impostor. Reused, unchanged, and weak passwords add to the threat of phishing attack.
- Loss of Control: Unorganized reporting of activities by employees using cloud services is escape door. They may copy the confidential data, overwrite, or delete with ease. Realizing the loss can be too late for introducing precautionary measures.
- Security Compliance Issues: Explicit regulatory control by government and industry standards has mandates that companies should know everything about their data. Repercussions of non-compliance or miss interpretations can affect at operational levels.
- Malware Injections: The scripts or codes embedded into cloud services behave as valid instances and run as SaaS (software as a service). The codes thus injected are viewable as part of the software or service within the cloud server themselves. Attackers can give tragic turns to the sensitive data.
- Malware Infections: Sensitive data encoded into video files uploaded on open social platforms. The cyber criminals use file-sharing services to spread the malware to targets for phishing attack. Exploitation of cloud services is mainly due to extensive use of cloud-based services.
- Insecure APIs: An application-programming interface allows customization of cloud services features to fit the business needs. API facilitates programmers by providing the tools to integrate applications with other software. Communication between two sites or applications risks the security.
- Shared Responsibilities: Cloud security provider and the client face vulnerabilities because of non-standard procedures of data protection. Compromising on shared responsibilities by one of the party can be dreadful.
- Inadequate Training: Cybersecurity threats of internal and external nature require rigorous training for the IT team. Latest security issues, knowledge to tackle them, and enrol management in the policies for decision-making.
What steps can be taken to bolster Application security in Azure Cloud, including investing in SDL and automating security assessments?
To design an environment for your applications on cloud, consider the following and secure them on Azure Cloud.
- Cloud Data Loss Prevention: Data can be stored on different cloud providers to allocate unified data access using Data Access Component. Setting up backup routine and recovery policies prevent data loss. Offline backups for cloud environment can maximize security. Ahead of the routines carefully check and review the backup procedures of the cloud service provider. Policies for strong passwords, multi-factor authentication (security question, voice verification, OTP, or biometrics), and no reuse of recent passwords can bring relief.
- Insider Threats: Best practices such as control on data access, surveillance on implementing technology, finely secured strategy and defined shared responsibilities can save the organizations from the insider threats. Minimize the risks of hijacking through proper permission management and setting perimeters for data required to perform tasks. IT processes should complement IT policies of the organization. It reduces the risks of downloading insecure applications by internal users. Pirated software videos, books, and games are inappropriate for the system health, bar the unauthorized downloading.
- Cloud Infrastructure: Protection and permissions to access data are the paths that do not meet instinctively. Compelling applications to maintain and assign rights to users is beneficial considering the criticality of infrastructure and Security in Azure Cloud. Improve software and data security with audit of privileged identity management, role-based access, limited access, time-bound access, temporary access, read-only access, and hierarchy.
- Application security: Enhance security in Azure Cloud through secured application design. Invest in SDL- Security Development Lifecycle, it being the most suitable time to fix the security issues. Assessment of operational security can be speedy by automating scanning of software, analyze the logs of Azure Security Centre, and Azure Web Application Firewall. Configure automated response to cyber attacks.
- Digital Identities: Increasing digital identities needs better management and tighter security. Need to sign in, frequent changes of passwords, authentication for data access adds burden of managing digital identities. Azure Active Directory supports Security in Azure Cloud by sharing same credentials of applications across devices. AD Connect replaces extinct identity integration tools that synchronize groups, user accounts, and passwords in the Azure AD on premise.
- Cloud Encryption: Encryption makes data unreadable and restricts its use. Decryption makes the data available for use. Security in Azure Cloud has two levels; symmetric encrypts and decrypts with your personal key while asymmetric uses public or private key to encrypt but to decrypt both if the keys are in pair. Encrypted data can be stored on physical servers or hard disks in case of attack decryption keys that do not accompany data can save data. Encryption facilitates data transition and eliminates the risk of exposure. Data classification under heads of private, public and restricted indicates the level of security needed. Azure Disk Encryption is available for Windows and Linux.
- Plan the non-regulatory: Loopholes in data protection laws raise the need to tighten the security over Azure Cloud. Employee monitoring has fewer restrictions and needs planning. The security is at risk when employees have high authority, they are upset with some situation or when serving notice period. Periodic system checks can be helpful. The joining and exit formalities of an employee could include precautions on crucial data, its access, and their responsibilities.
- Cybersecurity Training: Cloud security is a specialized skill and companies need to budget for the training of IT team. Technicalities and treatments should be practical and empowering. Hindrances caused to the users and applications are expensive than the training costs.
- Protection against Data Breach: Minor issues in the cloud environment that are unconcealed can be disastrous. The scripts with runtime access used beyond its permissions; can be blocked if controlled appropriately. Uploading sensitive data to cloud-based file sharing services are risk prone if the terms and conditions interpreted correctly.
- Architecture Complexities: App vulnerabilities affect the entire cluster on the cloud environment where you run your apps. Check if container-based platforms do manage the security else prepare to implement other security measures. Monitoring ports, multiple firewall settings, and loose codes will keep up the commitment of security in Azure Cloud.
- System Vulnerabilities: Operating systems, hosts, and components supporting the cloud environment should be secure. External security suites and community support lets you run more apps in cloud.
- Network Security: Limit the exposure at the network level between the system and applications by securing traffic flow amongst users, applications and internet. Azure Security Centre identifies internet-linked resources those are unsecured with a firewall or NVA – Network Virtual Appliances. Network Security Groups restrict unnecessary communication between virtual machines. They isolate applications amid environments, tiers, and services. Integrate existing network infrastructure to improve communication for linking the services in Azure. Denial of service for the internet facing endpoints builds Security in Azure cloud as it establishes internet connection only for trusted resources.
Swerve the focus from building heavy applications to securing them. Loss of customer trust and revenues is unaffordable and onerous.
Conclusion
In conclusion, prioritizing Security in Azure Cloud is imperative in today’s dynamic cloud landscape. This guide has explored key challenges in securing applications on Azure, from insider threats to external risks like DoS attacks.
At AnAr Solutions, we excel in designing highly secure Azure Cloud environments. Our expertise ensures your digital assets are safeguarded to the highest standards. Invest in the future resilience of your business with our tailored security solutions.