The alarming rise in cyberattacks targeting healthcare systems underscores the critical importance of healthcare data protection. Imagine the distress of discovering your private medical records, from health diagnoses to prescription details, have been publicly leaked. This scenario is not just hypothetical but a disturbing reality, as these breaches pose serious threats to patient confidentiality and trigger significant legal and financial repercussions for healthcare providers.
In 2023, the Department of Health and Human Services (HHS) documented an alarming 455 healthcare data breaches, impacting over 133 million individuals. These incidents transcend mere inconvenience, potentially leading to identity theft, discrimination, and substantial emotional distress for those affected. But what makes healthcare systems particularly vulnerable to such threats? In the following discussion, we’ll explore the inherent weaknesses within healthcare data security and outline strategic solutions to fortify your organization’s defenses against such pervasive cyber threats.
Identifying Key Vulnerabilities in Healthcare Data Protection
There are several key vulnerabilities contribute to this heightened risk:
- The digitization double-edged sword: The shift towards electronic health records (EHRs) undoubtedly improves accessibility and efficiency, but it also creates a vast digital landscape of sensitive data. This expanded attack surface becomes prime prey for malicious actors.
- Security awareness gap: Unfortunately, cybersecurity awareness among healthcare staff often lags behind. Busy schedules and complex systems can lead to lapses in following security protocols, creating openings for exploitation.
- Patchwork infrastructure: Many healthcare institutions operate with legacy systems not designed for the modern security landscape. Outdated software, disparate platforms, and inadequate monitoring create blind spots and vulnerabilities.
- Third-party woes: The reliance on third-party vendors for tasks like data storage or analytics introduces additional risks. Weak access controls or data breaches within these vendors can create ripple effects, impacting patient data across the network.
- Data deluge, security droughts: Healthcare generates massive amounts of data, from clinical records to financial information. Managing and securing this data avalanche can be overwhelming, leading to vulnerabilities and potential breaches.
How do rising cyber threats impact healthcare data security?
Rising cyber threats pose a significant and multifaceted impact on healthcare data security, challenging the integrity, confidentiality, and availability of patient information in several ways:
- Erosion of Patient Trust: The security of patient data is paramount to maintaining trust between healthcare providers and their patients. When cyberattacks compromise patient information, it can lead to a significant loss of trust, affecting the patient-provider relationship. Patients may become hesitant to share sensitive information, which can impact the quality of care they receive.
- Regulatory and Compliance Challenges: Healthcare organizations are subject to stringent regulatory requirements for data protection, such as HIPAA in the United States. Rising cyber threats increase the complexity of complying with these regulations. Failure to adequately protect patient data can result in severe penalties, legal actions, and damage to the organization’s reputation.
- Financial Burdens: The costs associated with responding to and recovering from cyberattacks can be substantial. Healthcare organizations must invest in forensic investigations, notification procedures, credit monitoring services for affected patients, and improvements to their cybersecurity infrastructure. Additionally, they may face fines for regulatory non-compliance and potential lawsuits from patients or other entities.
- Operational Disruptions: Cyberattacks, particularly ransomware, can disrupt healthcare operations, leading to delayed treatments, compromised patient care, and, in extreme cases, the necessity to divert emergency patients to other facilities. This not only affects the healthcare organization’s ability to provide care but can also have life-or-death consequences for patients.
- Innovation and Collaboration Hurdles: The threat of cyberattacks can deter healthcare organizations from sharing data, essential for innovation and improving patient care. This caution can impede collaborative digital health initiatives like telemedicine and remote monitoring, as well as the adoption of technologies reliant on data sharing, such as AI and machine learning, thereby stifling healthcare innovation and progress.
What key strategies can healthcare facilities take to secure patient data effectively?
In the modern digitalized healthcare environment, protecting patient information is more critical than ever. With cyber threats continuously advancing, implementing strong data protection measures is indispensable.
Below, we present practical suggestions from our experts to enhance your security measures and build trust with your patients:
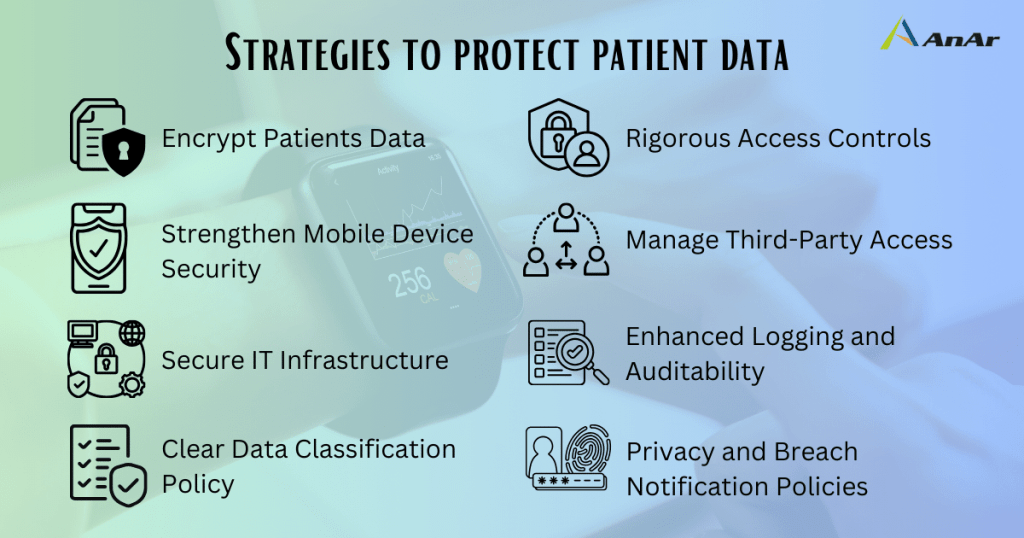
1. Encrypt Data at Every Stage
Implement industry-standard encryption algorithms like AES 256 to shield data at rest, in transit, and in use. Implement HTTPS and Transport Layer Security (TLS) for secure data movement.
Why It’s Essential?
Encryption acts as an impenetrable barrier, rendering patient data unreadable to unauthorized access, even during breaches. Minimizes data breach costs and legal ramifications.
2. Strengthen Mobile Device Security
Deploy a comprehensive Mobile Device Management (MDM) solution to oversee and secure devices accessing patient information. Restrict personal device usage or enforce strict security compliance.
Why It’s Essential?
As mobile devices become ubiquitous in healthcare, securing these endpoints is crucial to prevent them from becoming gateways for data breaches.
3. Secure Your IT Infrastructure
Apply the principle of least privilege across your network, ensuring users have access only to the information necessary for their roles. Regularly update and patch network devices and servers to protect against vulnerabilities.
Why It’s Essential?
A fortified IT infrastructure serves as your first line of defense, guarding patient data against ever-evolving cyber threats.
4. Adopt a Clear Data Classification Policy
Establish a systematic data classification policy to identify and apply appropriate security measures based on patient data sensitivity.
Why It’s Essential?
Not all data carries the same sensitivity or risk. Clear data classification helps in applying appropriate security measures to different types of data.
5. Enforce Rigorous Access Controls
Implement stringent access controls, including multi-factor authentication, to ensure only authorized personnel can access sensitive patient information.
Why It’s Essential?
Effective access controls ensure that only authorized personnel can access patient data, minimizing the risk of internal and external breaches.
6. Regulate Data Retention and Deletion
Implement a comprehensive data retention policy aligned with regulations like HIPAA and GDPR. Establish clear guidelines for how long each type of data needs to be stored based on legal, clinical, and business requirements. Ensure secure deletion of data exceeding retention periods using certified methods like disk wiping or data shredding. Support patient rights to data deletion by providing a clear and accessible process for them to request and manage their data.
Why It’s Essential?
Mitigates compliance risks and potential fines. Minimizes the attack surface by reducing stored data. Empowers patients and fosters trust.
7. Manage Third-Party Access
Limit third-party data access to the minimum required for specific tasks. Prioritize data minimization strategies like pseudonymization or tokenization for sensitive information. Implement multi-factor authentication and granular access controls for third-party vendors. Employ data masking or obfuscation to further safeguard sensitive data in transit and at rest. Obtain explicit patient consent for all third-party data access.
Why It’s Essential?
Minimizes the risk of data breaches through compromised third-party vendors. Protects patient privacy and complies with data protection regulations.
8. Enhance Logging and Auditability
Implement a centralized log management system that captures all data access and activity across your IT infrastructure. Ensure logs are tamper-proof and securely stored. Conduct regular audits of data systems and third-party vendors using qualified security professionals. Analyze logs for suspicious activity and potential breaches.
Why It’s Essential?
Detailed logging and regular audits provide visibility into data access and modification, enabling the early detection of unauthorized activities and potential vulnerabilities.
9. Establish Privacy and Breach Notification Policies
Develop clear and easily accessible privacy policies outlining your data collection, use, and storage practices. Define a comprehensive breach notification policy detailing steps you will take in the event of a data breach, including who will be notified and how. Regularly review and update these policies to reflect changes in regulations and best practices.
Why It’s Essential?
Transparency in privacy policies fosters patient trust, while effective breach notification policies ensure compliance with regulations and mitigate the impact of data breaches.
10. Conduct Regular Assessments
Conduct regular vulnerability assessments and penetration testing to identify and address potential security risks in your IT infrastructure and applications. Prioritize patching critical vulnerabilities promptly. Partner with qualified security professionals to conduct these assessments and ensure adherence to best practices.
Why It’s Essential?
Ongoing assessments help identify potential vulnerabilities, allowing for timely remediation and strengthening of defences against cyber threats.
Conclusion
The progression of digital healthcare introduces significant opportunities alongside challenges, particularly in the realm of protecting patient information. Adopting strategic approaches to bolster data security is crucial for effectively managing the intricacies of cybersecurity threats and meeting regulatory requirements, especially within the cybersecurity in healthcare sector.
AnAr Solutions stands at the forefront of addressing these challenges, offering tailored IT consulting and security solutions to healthcare organizations worldwide. Our expertise in the latest technologies and deep understanding of healthcare regulations enable us to equip our clients with cutting-edge defences against cyber threats. We are dedicated to ensuring that healthcare providers can maintain the highest standards of data security, safeguarding patient information and fostering trust.