Discover the critical steps healthcare providers can take to protect patient data against rising cyber threats. From encryption to third-party risk management, learn how to build a robust defense.
Security
Angular Overview: A framework developed and maintained by Google. It lets you build single page applications (SPA) with opensource language…
Cloud native application is a lightweight container based virtual and shared infrastructure. We develop cloud native applications in different programming…
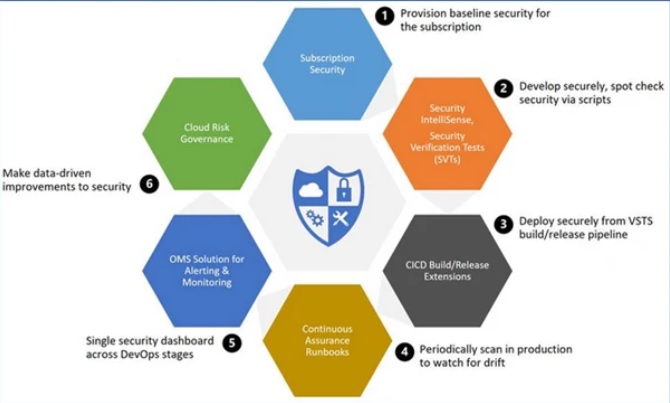
Securing your confidential business and customer data is of paramount importance, especially in the ever-evolving landscape of cloud computing. In…
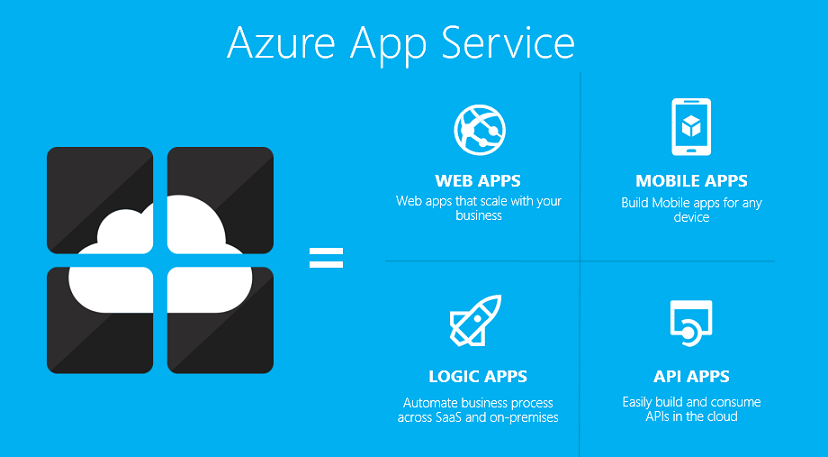
Azure App Services allows you to choose the development platform from varied programming languages. Develop and deploy web applications in…
Outsourcing is crucial part of modern day business. Every industry tries to cut the expense ratio for profitability and sustainability….
Software Security In today’s world everyone is very concerns about privacy. We like to ensure data about ourselves is not…
Application Security Best Practices In the industry surveys extending from Symantec Threat Reports to the Gartner analyst report, the application…
Secure Coding – With the scare of recent cyber crimes and leaks occurring over the internet even with the deepest…
In my previous blog, we discussed about Pentesting using ZAP tool, today we discuss the remaining 3 points of security…
Progressive web apps are able to deliver an app-like experience for its users over the web using advanced capabilities that…
Developing an application for healthcare applications involves a survey of paperwork from different sources. As the HIPAA regulates over all…
The demand for security tests within companies is increasing. These tests can be executed in different ways, each with its…
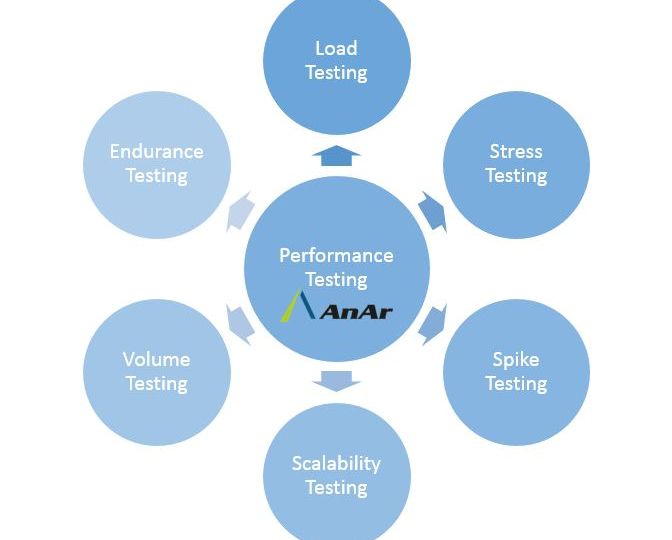
Performance testing is defined as the technical investigation done to determine or validate the speed, scalability, and/or stability characteristics of…
Before we divulge into the possibilities of secure cookies, it is imperative to discuss the history of cookies. For this…
Guarding your software against threats, defects, and bugs in the early stages is an important means to secure your code….