Healthcare with SharePoint- Today we talk about how SharePoint can be effectively utilized within healthcare organization , how SharePoint helps…
Best Practices
Modular CSS is a concept that will help you write more maintainable and readable code. It is compatible with any…
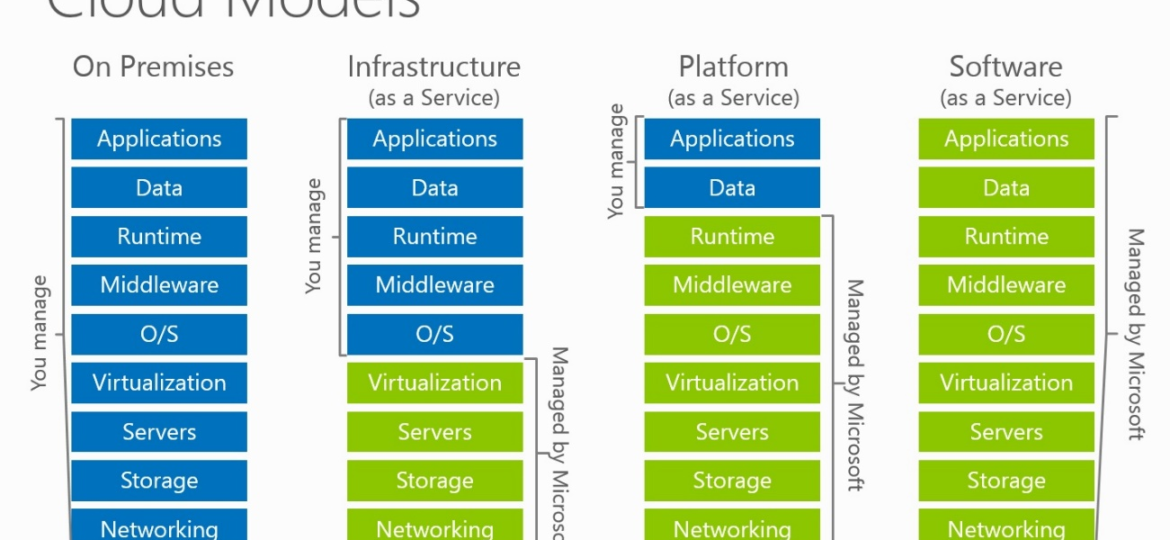
Azure is based on cloud computing that manages the application of the web, mobile API, and logical features. It works…
Every organisation has to follow certain steps within protocols to follow for vulnerability assessment for a legacy system. It is important…
The verification for the web API is impartial using the token, sent with the existing request. This is basically done…
A Package Manager is software that automates the process of maintaining software applications in a system. It is a collection…
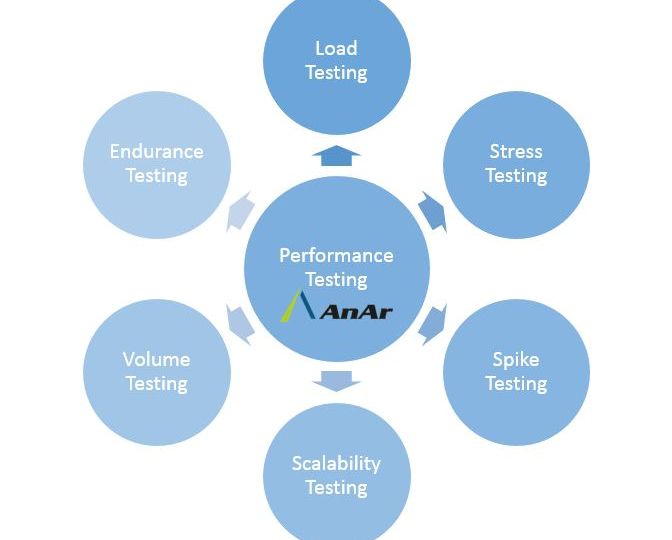
Performance testing is defined as the technical investigation done to determine or validate the speed, scalability, and/or stability characteristics of…
When it comes to making the choice of a .NET framework to build your web applications on, there are two…
Before we divulge into the possibilities of secure cookies, it is imperative to discuss the history of cookies. For this…
Programmers are familiar with the term Angular as they associate it with API and application development. Angular is a platform…
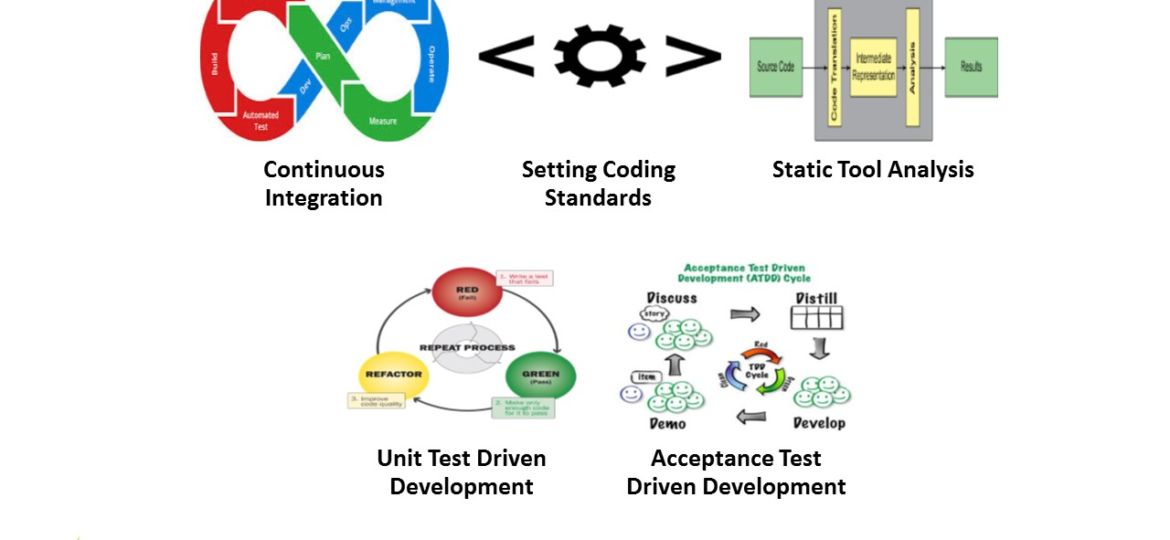
Guarding your software against threats, defects, and bugs in the early stages is an important means to secure your code….
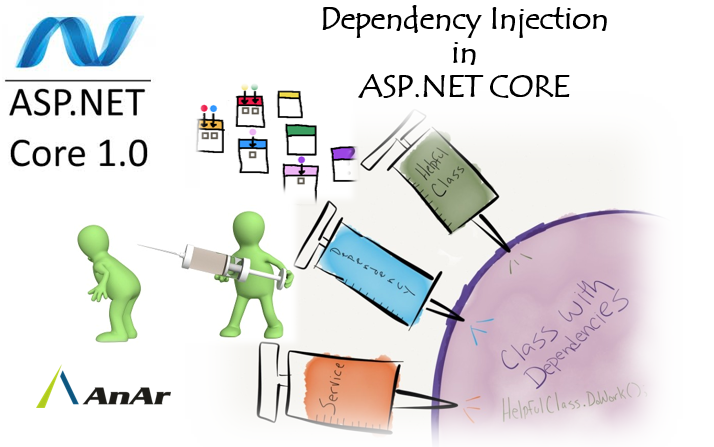
The Dependency Injection pattern is a implementation of Inversion of Control. Inversion of Control (IoC) means that objects do not…
Internet of Things (IoT), the latest advancement that Information Technology has to offer is now upgraded from a simple self-built…
As most assets of an organization are available on servers, the external threat is imminent, and one must be prepared…
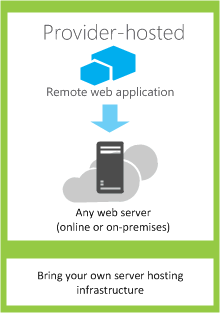
Introduction for Provider Hosted Apps: Provider Hosted App is one where the app is hosted outside of SharePoint. For Example,…
There is a saying that quality is a free commodity provided one invests in improving it. The major problem with the legacy…