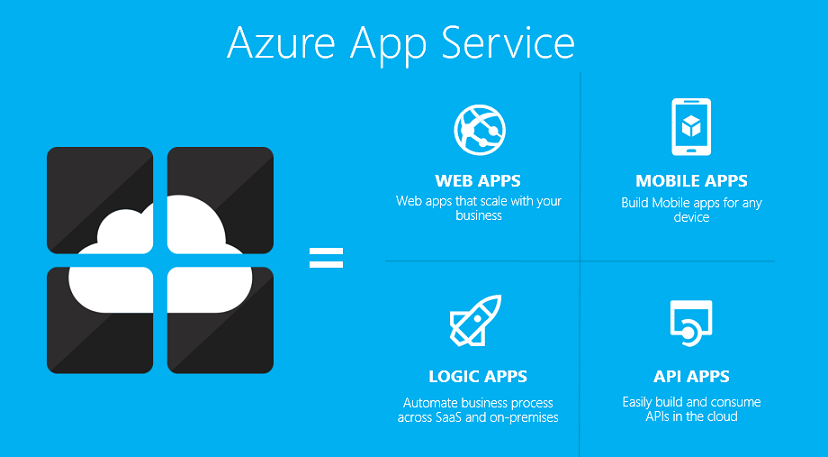
Azure App Services allows you to choose the development platform from varied programming languages. Develop and deploy web applications in…
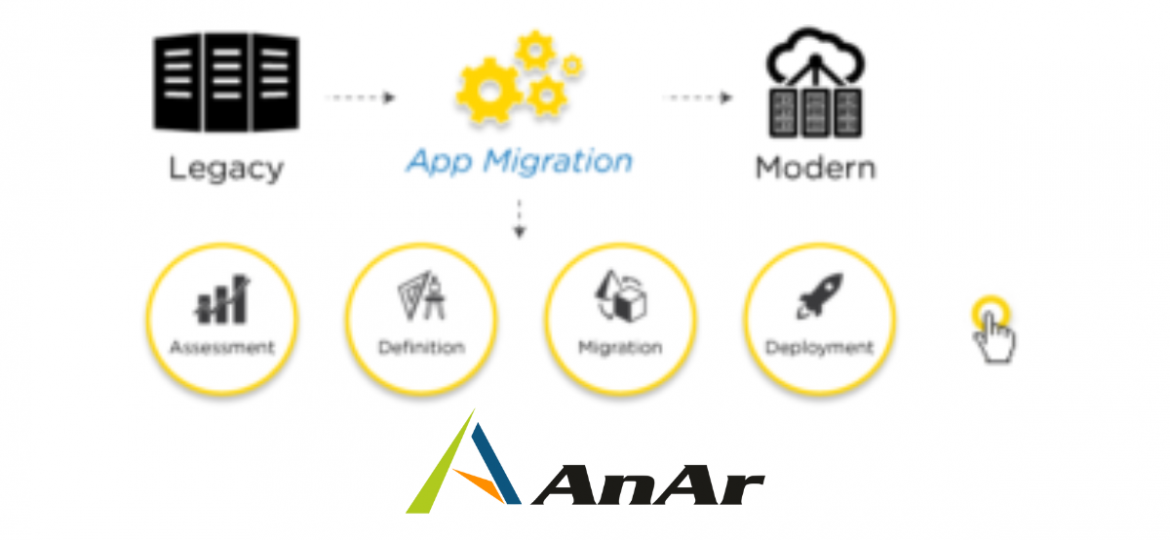
AnAr Processes
Which cloud migration approach is right for your business? – Re-host, re-platform or replace? Deciding factors differ from companies due…
Dealing with legacy code can be a chore. Some developers even call it “legacy code hell”.
But, unless you’re starting a project from scratch, legacy code is inevitable. And that means you need a better way to work with it.
Software is traditionally divided into two categories: packaged or custom. Custom software, also known as “Bespoke” software, is a type…
Top 5 Requirements Elicitation Techniques In a software development scenario, solid elicitation abilities are a must have for everyone indicted…
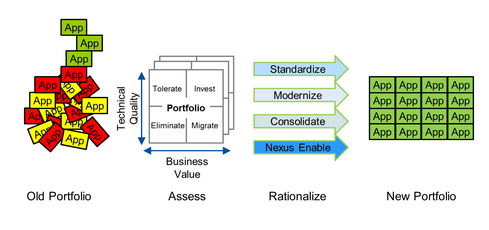
Application Rationalization Continuing financial insecurity is commanding stern cost burdens on organizations across businesses. In reply, a lot of industries…
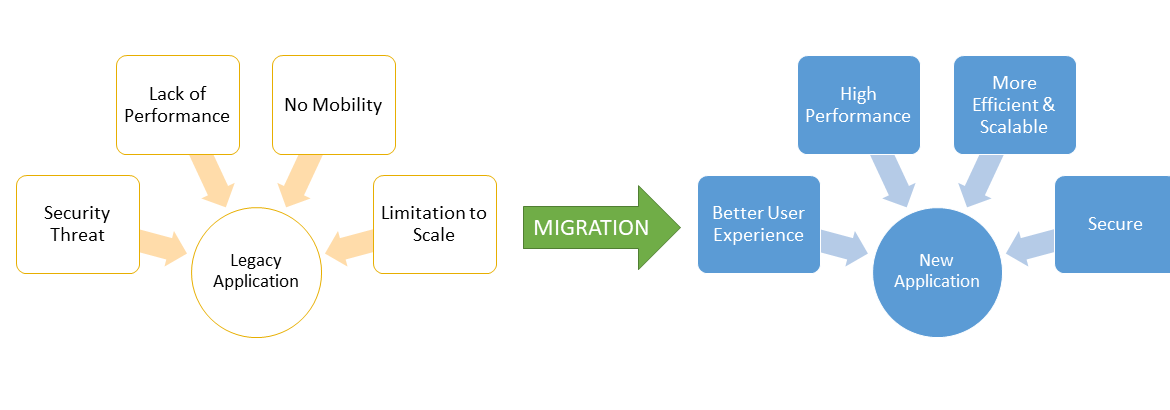
While speaking about multi-billion-dollar businesses, Legacy is considered as wealth, wisdom and status. In terms of software, legacy is often…
Definition of Done (DoD) is mostly a software development word and is used in agile software development and agile project management….
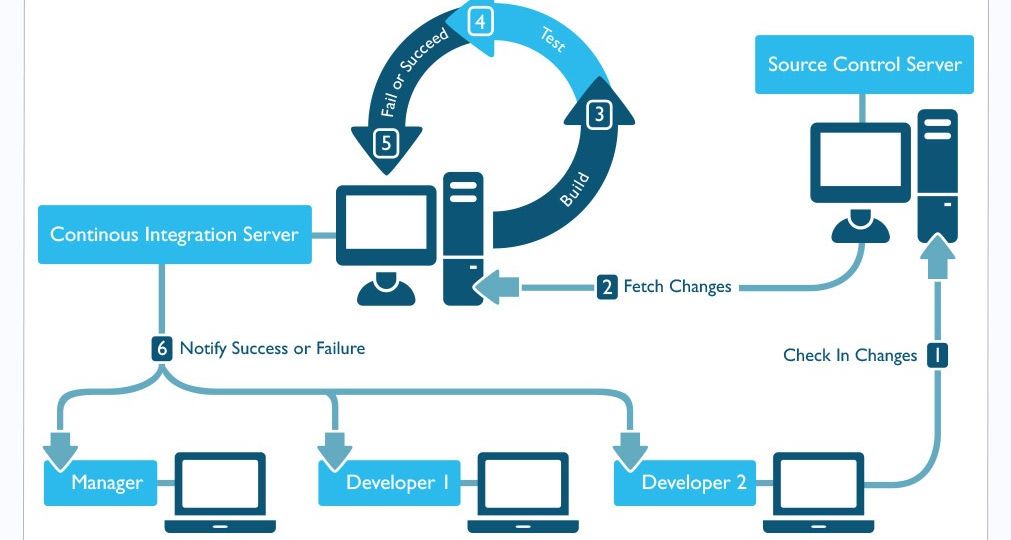
CI or Continuous Integration is a term used in DevOps that allows real time integration of data into the central…
Mobile phones are a part of life, to this extent that one cannot stay without a checking his/her phone once…
In my previous blog, we discussed about Pentesting using ZAP tool, today we discuss the remaining 3 points of security…
Hybrid involves the amalgamation of two distinct things into one thing to produce some better result. Hybrid IT is therefore…
Developing an application for healthcare applications involves a survey of paperwork from different sources. As the HIPAA regulates over all…
Impact Analysis is a key aspect of responsible requirements management. It provides accurate understanding of the implications of a proposed…
Estimation Tips for Building Self Managing Teams Offshore Team has committed the deliverable for Friday morning and it is Monday…
Every organisation has to follow certain steps within protocols to follow for vulnerability assessment for a legacy system. It is important…