Application Security and Cloud Native Apps
We came across many clients who have started their cloud migration journey and moved their on-premise applications to public or private cloud. Such migrations have provided some benefits in terms of availability. These monolithic applications could not take advantage of cloud offerings to truly leverage it potential. As part of next phase of migrations, many applications have been built by following microservices architecture and it helped organizations to build scalable systems.
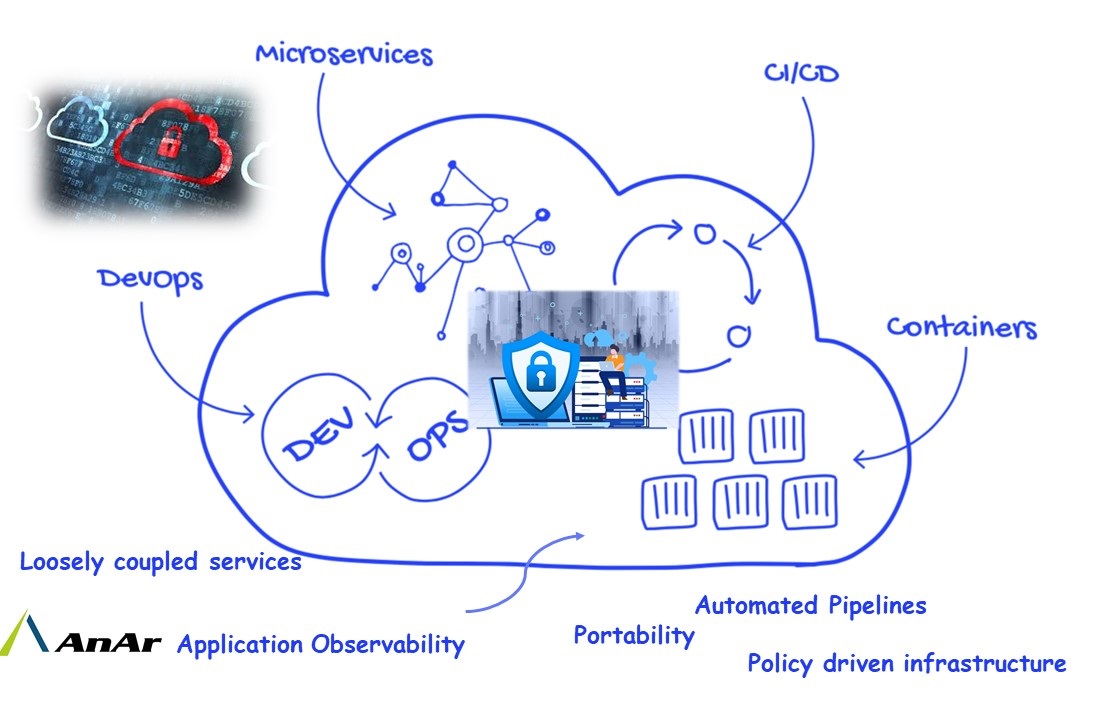
While developing microservice architecture based application, organizations have leveraged DevOps and containerized deployments to improve on the speed of deployments and minimum downtimes. Though new systems have been built using Microservices and Kubernetes, those were still far away from being cloud native. Many times people refer to applications as cloud native which are using microservices and containers, which is not completely true.
Cloud Native pattern focuses on application observability, portability, loosely coupled services, policy driven infrastructure and automated pipelines. Without observability which encompasses log aggregation, monitoring and metric collection, we will not able to gain insights into the system. Portability has proved its importance by allowing developers to write code once and run it anywhere. Microservices have already providing advantages of loosely couples services. This allows applications to run, scale and interact as an independent entity. Ops team gets an ability to define desired state of application and infrastructure using definition files and easily able to enforce infrastructure policies. Automated pipelines have already removed manual interventions in shipping code to production.
Cloud Native tools and patterns help organizations to achieve their product goals and along with these combinations of tools organization must focus on application security in cloud native context. Just using cloud native tools will not help you with application security, in fact most reported cloud breaches are due to misconfiguration, mismanaged credentials and not due to cloud provider. Blind adoption of cloud native tools can introduce many vulnerabilities. We at AnAr work with our clients to implement properly prepared cloud native patterns which can help application security embedded into faster and agile development cycle.
Best Regards,
Rupashri
